The Silent S in HTTPS
Why http(s) is not secure?
Before we start to learn about what is HTTPS, let us first know the benefits:
1. HTTPS makes your website less vulnerable to cybercrimes
Let’s say you have a website that brings your customers to a third-party page where they make purchases using a credit card. If your site isn’t secured with HTTPS, or it is set up incorrectly, bad actors can intercept the content of your website, then easily create the exact same payment page they can control and allow them to see and capture each credit card number your customers submit. Having to resolve customer complaints due to lax site security resulting in credit card theft could be fatal to your business.
2. Google tends to rank secure websites higher than websites without HTTPS
When Google changed its algorithm back in 2014, we saw a 60–70% increase in SSL update among millions of websites out there. Websites that become HTTPS secure got ranked higher, while the ranking of websites without HTTPS slightly dropped.
Sooner or later, HTTPS will become a standard consumers demand, and websites will need to have it in order to come across as trustworthy, reliable, and secure.
3. A secure website gives you a better reputation
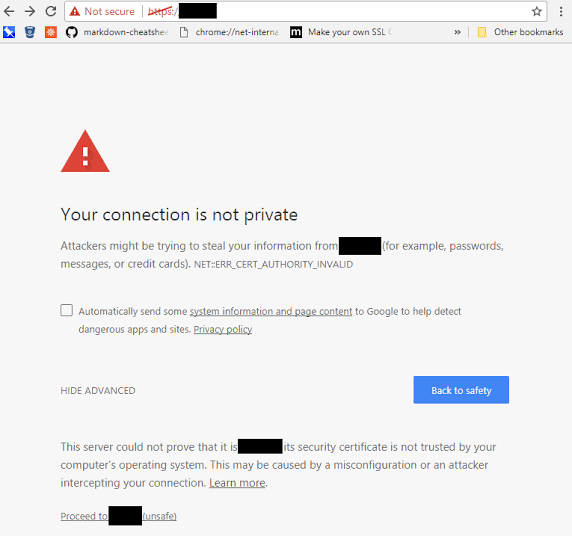
If visitors come to your website and can see your site information can be easily intercepted, it definitely does not give a good impression. If your website is not safe, secure, and reliable, what makes you think your customers would risk purchasing from you when they can purchase similar products/services from your competitors with more secure websites?
To ensure you maintain your company’s and brand’s good reputation, you should make a good first impression by showing that your site is HTTPS secured.
HTTPS (Secure Hypertext Transport Protocol)
HTTPS is a secure version of HTTP. This ensures that any communication sent online is secured by the SSL/TLS connection. Any ongoing communication between the server and browser will be encrypted for your safety. It allows you to evaluate how secure the environment is. If you are looking to establish an HTTPS connection, you will have to first purchase an SSL certificate from someone you can trust. You don’t want to purchase a certificate from just anyone. Look for trusted certificate authority. Then, you need to install it on the proper server.
HTTPS is the code-text that is written using standard HTTPS format and secured with SSL/TLS to encrypt the HTTP text and ensure the communication is protected at all times.
There are a number of reasons to use an HTTPS connection:
It helps to establish a secure communication between server and browser.
It secures websites against tampering activities or eavesdropping.
It protects users from man-in-the-middle attacks.
It is used worldwide by business of all sizes to process secure payment transactions.
It is used by banking, healthcare, eCommerce, social media, and government industries.
Regardless of what your situation might be, you need to look into the benefits of implementing SSL, HTTPS, and TLS secure connections in your business. You never know just how beneficial these secure methods are until you have to use them.
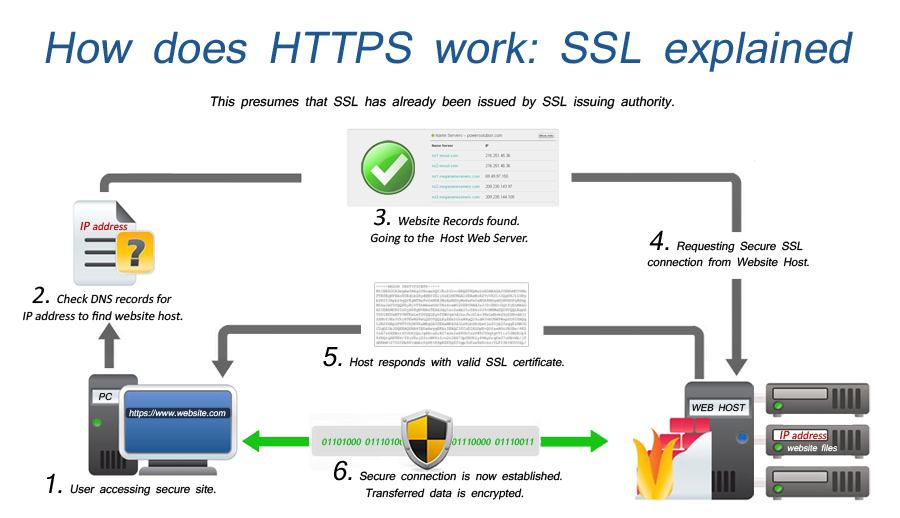
In HTTPS, how does TLS/SSL encrypt HTTP requests and responses?
TLS uses a technology called public key encryption: there are two keys, a public key and a private key, and the public key is shared with client devices via the server’s SSL certificate. When a client opens a connection with a server, the two devices use the public and private key to agree on new keys, called session keys, to encrypt further communications between them.
All HTTP requests and responses are then encrypted with these session keys (this takes place at layer 6 in the OSI model), so that anyone who intercepts communications can only see a random string of characters, not the plaintext.
But HTTPS doesn’t always mean the site is safe
Let’s be honest, when most people see a little green lock with the word “Secure” to the left of a URL, they think the site is safe. Ditto for spotting the words “this site uses a secure connection” or a URL beginning with the letters “https.” More and more sites these days are switching to HTTPS. Most have no choice, in fact. So what’s the problem? The more secure sites there are, the better — right?

We’re about to let you in on a little secret: Those “Secure” symbols don’t guarantee a website is safe from all threats. A phishing site, for example, can legitimately display that comforting green lock next to its https address. So, what’s going on? Let’s find out.
A secure connection does not mean a secure site
The green lock means that the site has been issued a certificate and that a pair of cryptographic keys has been generated for it. Such sites encrypt information transmitted between you and the site. In this case, the page URLs begin with HTTPS, with the last “S” standing for “Secure.”
Sure, encrypting transmitted data is a good thing. It means that information exchanged between your browser and the site is not accessible to third parties — ISPs, network administrators, intruders, and so on. It lets you enter passwords or credit card details without worrying about prying eyes.
But the problem is that the green lock and the issued certificate say nothing about the site itself. A phishing page can just as readily get a certificate and encrypt all traffic that flows between you and it.
Put simply, all a green lock ensures is that no one else can spy on the data you enter. But your password can still be stolen by the site itself, if it’s fake.
Phishers make active use of this: According to Phishlabs, a quarter of all phishing attacks today are carried out on HTTPS sites (two years ago it was less than 1 percent). Moreover, more than 80 percent of users believe that the mere presence of a little green lock and the word “Secure” next to the URL means the site is safe, and they don’t think too hard before entering their data.
How not to fall for the bait
To sum up, the presence of a certificate and the green lock means only that the data transmitted between you and the site is encrypted, and that the certificate was issued by a trusted certificate authority. But it doesn’t prevent an HTTPS site from being malicious, a fact that is most skillfully manipulated by phishing scammers.
So always be alert, no matter how safe the site seems at first glance.
Never enter logins, passwords, banking credentials, or any other personal information on the site unless you are sure of its authenticity. To do so, always check the domain name — and very carefully; the name of a fake site might differ by only one character. And ensure links are reliable before clicking.
Always consider what a particular site is offering, whether it looks suspicious, and whether you really need to register on it.
SSL (Secure Socket Layer)
SSL was created by Netscape Communications Corporation back in 1994. It was designed to create a secure internet communication via the Web. It is a standard protocol that encrypts communication between your browser and the server, and allows for private information like social security numbers, credit card details, and login credentials to be transferred easily over the Internet.
SSL utilizes two keys:
Public keys that are knowable by everyone.
Private keys known only by the person receiving the message.
The two keys work together to form an encrypted connection via the Web.
Being able to connect to a specific port requires a secure connection. As an example, you would use port 443 for HTTPS, 995 for secure POP3, 993 for secure IMAP, and so on. All of these ports are already set up on the server. They are ready to negotiate secure connections first, then they will proceed to do whatever else you need after that.
How does HTTPS help authenticate web servers?
Authentication means verifying that a person or machine is who they claim to be. In HTTP, there is no verification of identity — it’s based on a principle of trust. The architects of HTTP didn’t necessarily make a decision to implicitly trust all web servers; they simply had priorities other than security at the time. But on the modern Internet, authentication is essential.
Just like an ID card confirms a person’s identity, a private key confirms server identity. When a client opens a channel with an origin server (e.g. when a user navigates to a website), possession of the private key that matches with the public key in a website’s SSL certificate proves that the server is actually the legitimate host of the website. This prevents or helps block a number of attacks that are possible when there is no authentication, such as:
Man-in-the-middle attacks
DNS hijacking
BGP hijacking
Domain spoofing
HTTPS myth-conceptions (src: CloudFlare)
Many websites have been slow to adopt HTTPS. To explore why this is the case we have to look at the history.
When HTTPS initially began rolling out, proper implementation was hard, slow, and expensive; it was hard to implement properly, slowed down Internet requests, and increased costs by requiring expensive certificate services. None of these impediments remain true, but a lingering fear still exists for a lot of website owners, which has impeded some taking the leap into better security. Let’s explore some of the myths about HTTPS.
“I don’t handle sensitive information on my website so I don’t need HTTPS”
A common reason websites don’t implement security is because they think it’s overkill for their purposes. After all, if you’re not dealing with sensitive data, who cares if someone is snooping? There are a few reasons that this is an overly simplistic view on web security. For example, some Internet service providers will actually inject advertising into HTTP-served websites. These ads may or may not be in line with the content of the website, and can potentially be offensive, aside from the fact that the website provider has no creative input or share of the revenue. These injected ads are no longer feasible once a site is secured.
Modern web browsers now limit functionality for sites that are not secure. Important features that improve the quality of the website now require HTTPS. Geolocation, push notifications and the service workers needed to run progressive web applications (PWAs) all require heightened security. This makes sense; data such as a user’s location is sensitive and can be used for nefarious purposes.
“I don’t want to damage my website’s performance by increasing my page load times”
Performance is an important factor in both user experience and how Google returns results in search. Understandably, increasing latency is something to take seriously. Luckily, over time improvements have been made to HTTPS to reduce the performance overhead required to set up a encrypted connection.
When an HTTP connection occurs, there are a number of trips the connection needs to make between the client requesting the webpage and the server. Aside from the normal latency associated with a TCP handshake (shown in blue below), an additional TLS/SSL handshake (shown in yellow) must occur to use HTTPS.
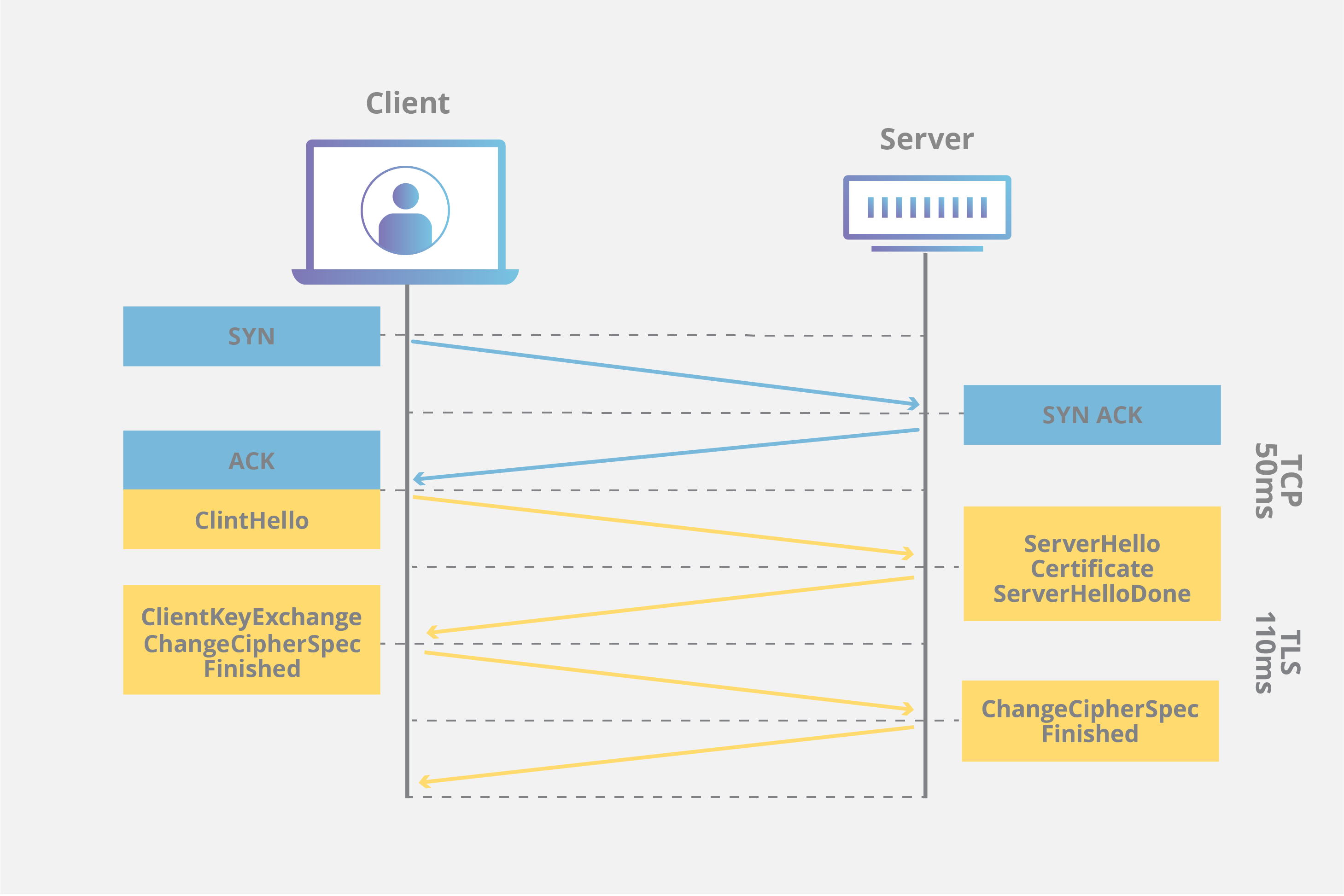 src: CloudFlare
src: CloudFlare
Improvements can be implemented to reduce the total latency of creating a SSL connection, including TLS session resumption and TLS false start.
By using session resumption a server can keep a connection alive for longer by resuming the same session for additional requests. Keeping the connection alive saves time spent renegotiating the connection when the client requires an uncached origin fetch, reducing the total RTT by 50%.
Another improvement to the speed at which an encrypted channel can be created is to implement a process called TLS false start, which cuts down on the latency by sending the encrypted data before the client has finished authentication.
Last but not least, HTTPS unlocks performance enhancements using HTTP/2 that let you do cool things like server pushing and multiplexing which can greatly optimize performance for HTTP requests. In total there is a significant performance benefit for making the switch.
“It’s too expensive for me to implement HTTPS”
At one point this may have been true, but now the cost is no longer a concern.
“I’m going to lose search ranking while migrating my site to HTTPS”
There are risks associated with website migration, and done improperly a negative SEO impact is possible. Potential pitfalls include website downtime, uncrawled webpages, and penalization for content duplication when two copies of the site exist at the same time. That said, websites can be migrated safely to HTTPS by following best practices.
Two of the most important migration practices are:
- using 301 redirects and 2) the proper placement of canonical tags. By using server 301 redirects on the HTTP site to point to the HTTPS version, a website tells Google to move to the new location for all search and indexing purposes. By placing canonical tags on the HTTPS site only, crawlers such as Googlebot will know that the new secure content should be considered canonical going forward.
If you have a large number of pages and are concerned that the recrawl will take too long, reach out to Google and tell them how much traffic you’re willing to put through your website. The network engineers will then crank up the crawl rate to help parse your site quickly and get it indexed.
Stay Curious!
